The Linux Hack was an inside job…
Summary
TLDRThe video discusses a serious security back door discovered in a widely used Linux compression utility, XZ utils, by developer Andres Frey. The malicious code, which could allow unauthorized remote access, was detected before causing widespread issues. Additionally, the video covers Amazon's decision to abandon its cashierless checkout system in favor of Dash Carts and Google's agreement to delete a large store of web data collected via Chrome's incognito mode, updating their privacy policy to better inform users of data collection practices.
Takeaways
- 🔍 A serious security back door was discovered in a widely used compression utility for Linux, XZ utils, by developer Andres Frey from Microsoft.
- 🕵️♂️ The vulnerability was found by chance during micro benchmarking, which revealed excessive CPU usage with encrypted logins related to the exed compression library.
- 🚨 The malicious code was present in beta releases for Fedora Rawhide, Debian, and a stable release of Arch Linux, but was caught before widespread exploitation.
- 💡 The back door functioned by injecting code during SSH authentication, potentially allowing unauthorized remote access.
- 👤 The code appears to have been introduced by one of XZ utils' primary developers, giaan AKA GIA, who had been contributing since 2021.
- 🤔 It is theorized that GIA's involvement may have been part of a long-term scheme to gain increasingly invasive permissions within the project.
- 🛒 Amazon is discontinuing its cashierless checkout system, 'Just Walk Out', in its fresh grocery stores due to reliance on human oversight.
- 👁️ Amazon's system required an estimated 70% of sales to be reviewed by human monitors, contrary to the fully automated impression the company had given.
- 📃 Google has agreed to delete a large cache of web data collected while users browsed in Chrome's incognito mode as part of a class action lawsuit settlement.
- 🔒 Google will also update its privacy policy and incognito mode landing page to clarify that data collection continues regardless of browsing mode.
- 🏅 Qualcomm's new Snapdragon X Elite laptop processors have outperformed Intel's Meteor Lake Core Ultra chips in benchmarks, showing 50% faster performance at half the power consumption.
Q & A
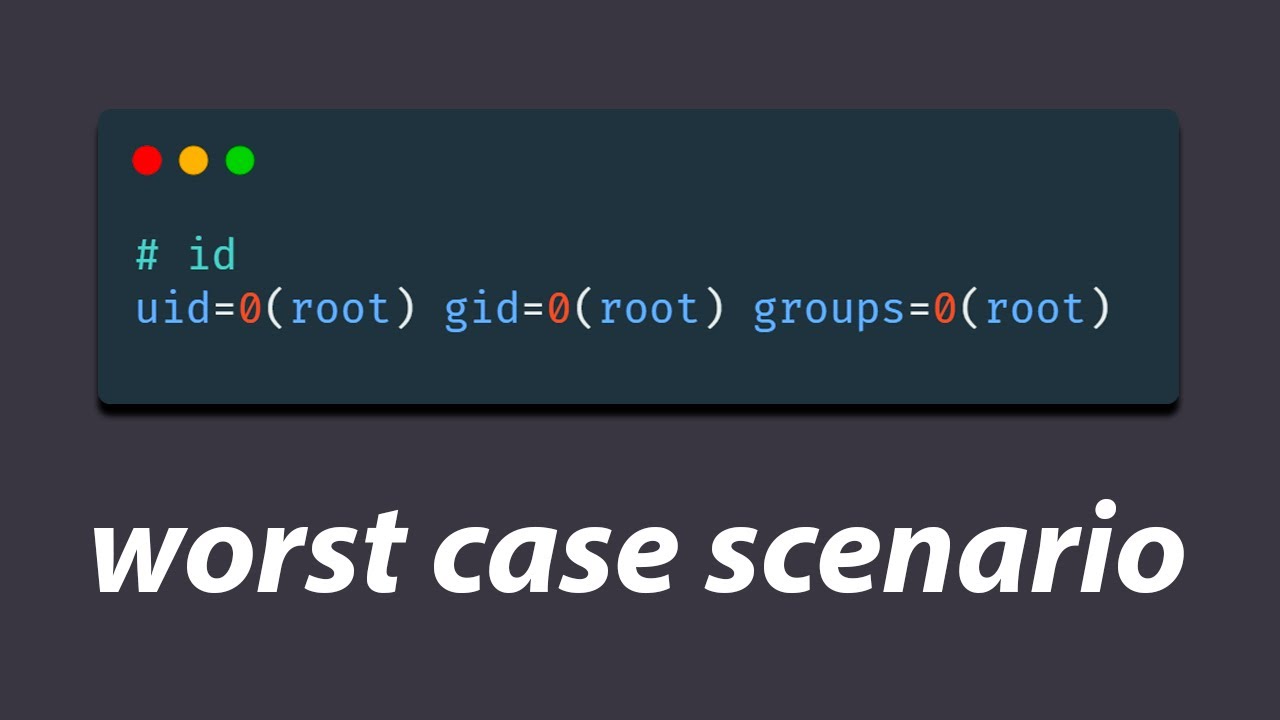
What security issue was discovered in a widely used compression utility for Linux?
-A serious security back door was discovered in the XZ utils, a compression utility for Linux, which could potentially allow unauthorized remote access by injecting code during SSH authentication.
Who discovered the security back door in XZ utils and how did they notice it?
-Andres Frey, a developer who works for Microsoft by day and maintains PostgreSQL by night, discovered the security back door. He noticed the issue while doing micro benchmarking during his Easter Long Weekend and observed that encrypted logins to part of the XZ utils compression library were using an unusually high amount of CPU.
Which distributions of Linux were found to have the malicious code in their beta releases?
-The malicious code was found in beta releases for Fedora Rawhide, Debian, and a stable release of Arch Linux.
What is the speculated motive behind the introduction of the malicious code in XZ utils?
-It is theorized that one of the primary developers of XZ utils, giaan AKA GIA (also known as t75), may have introduced the malicious code as part of a long con to gain increasingly invasive permissions through genuine code contributions and a pressure campaign against the original developer, Lassie Colin.
What was the original purpose of Amazon's cashierless checkout system, 'Just Walk Out'?
-The 'Just Walk Out' system was designed to allow customers to scan in at the door, take the items they want, and automatically be charged for them upon exiting the store without the need for a cashier.
How accurate was the portrayal of Amazon's 'Just Walk Out' system being fully automated?
-The portrayal was inaccurate as an estimated 70% of 'Just Walk Out' sales required a human review. The system relied on a small army of over a thousand overseas workers to monitor and review transaction footage.
What has Google agreed to do as part of a settlement in a class action lawsuit?
-Google has agreed to delete a massive store of web data collected while users browsed using Chrome's incognito mode. They have also agreed to update their privacy policy and the incognito mode landing page to explicitly notify users that data is still collected from third-party sites and apps, regardless of the browser mode.
What new security feature is Google testing to prevent unauthorized access to sensitive accounts?
-Google is testing Vice bound session credentials, a form of encryption that ties authentication cookies to the user's PC, to block malicious actors from accessing sensitive accounts by stealing and cloning a person's session credentials.
How did TSMC respond to the strongest earthquake in 25 years in Taiwan?
-Workers at TSMC returned to factories less than 24 hours after the earthquake. Within 10 hours of the earthquake, 70% of TSMC's chip operations had recovered.
What is Australia's solution to the problem of large animal detection systems failing to detect kangaroos?
-Australia is turning to virtual fences, which are activated by approaching headlights and use flashing lights and high-pitched alarms to scare animals away from roadsides.
What unusual event occurred in Naples, Florida, allegedly related to the International Space Station?
-A 2B piece of cylindrical metal, allegedly part of a 2.9-ton cargo pallet containing nine batteries that was tossed from the ISS three years ago, ripped through the roof and two floors of a home in Naples, Florida.
Outlines
🔍 Security Flaw in Linux Compression Utility
A serious security back door was discovered in a widely used compression utility for Linux, called xed utils, by Andres Frey, a developer at Microsoft. The vulnerability was found during micro benchmarking over Easter Long Weekend, when an unusually high CPU usage was detected during encrypted logins. The back door was present in xed utils, which is available for almost every Linux distribution. Fortunately, the malicious code was identified before being integrated into a major distribution's production release. It was detected in beta releases for Fedora Rawhide, Debian, and a stable release of Arch Linux. The back door functions by injecting code during SSH authentication, potentially allowing unauthorized remote access. The malicious code is suspected to have been introduced by one of the primary developers of XZ utils, giaan AKA GIA, who had been contributing to the project since 2021. Researchers are yet to find any evidence of gean's existence beyond his involvement in open-source circles.
🛒 Amazon's Cashierless Checkout System and Google's Privacy Update
Amazon is discontinuing its cashierless checkout system, 'Just Walk Out', across its chain of fresh grocery stores due to its reliance on a large number of overseas workers to monitor transactions, contrary to the fully automated impression it gave. The system used a network of cameras and sensors to track customers and charge them for items upon exiting the store. However, an estimated 70% of these sales required human review. Amazon disputes this figure, stating that reviewers primarily annotated videos for machine learning improvements. In a separate development, Google has agreed to delete a vast amount of web data collected through Chrome's incognito mode as part of a class action lawsuit settlement. Google will also update its privacy policy and the incognito mode landing page to clarify that data is still collected from third-party sites and apps, regardless of browsing mode. This follows Google's initial argument that users had implicitly consented to data collection in incognito mode because they were warned that their activity might still be visible to visited websites.
🚀 Tech Innovations and Updates
Qualcomm has released new benchmarks for its upcoming ARM-powered Snapdragon X Elite laptop processors, showing impressive performance and power efficiency, outperforming Intel's Meteor Lake Core Ultra chips, AMD's Ryzen 9 7940 HS, and even Apple's M3. This comes ahead of the processors' anticipated arrival in Microsoft's new Surface lineup. In other news, Google Podcasts will be discontinued, with users outside the US able to access podcasts until June 24th. TSMC, a major chip manufacturer responsible for 80-90% of the world's high-end chips, quickly resumed operations after a strong earthquake in Taiwan, with 70% of chip operations recovered within 10 hours. Australia is considering virtual fences to address issues with vehicle large animal detection systems, particularly with kangaroos, which have proven difficult to calibrate. Finally, a piece of space debris, allegedly from the International Space Station, crashed through a house in Naples, Florida, raising questions of liability for damages.
Mindmap
Keywords
💡Security Backdoor
💡Linux
💡Andreas Frey
💡SSH Authentication
💡XZ Utils
💡GIA (gian AKA GIA)
💡Amazon Go
💡Dash Cart
💡Incognito Mode
💡Session Credentials
💡TSMC
💡Virtual Fences
Highlights
A serious security back door was discovered in a widely used compression utility for Linux.
The security issue was flagged by developer Andres Frey, who works for Microsoft and maintains PostgreSQL.
The back door was discovered during micro benchmarking over the Easter Long Weekend.
Encrypted logins using the exed compression Library were found to be consuming an unusually high amount of CPU.
The malicious code was found in xed utils, which is available for almost every distribution of Linux.
The code was detected before being added to the production release of a major distribution.
The back door was present in beta releases for Fedora Rawhide, Debian, and a stable release of Arch Linux.
The back door works by injecting code during SSH authentication, potentially allowing unauthorized remote access.
The malicious code may have been introduced by one of XZ utils' primary developers, Giaan AKA GIA.
GIA's involvement in XZ has been suspected to be part of a long con to gain more invasive permissions.
Amazon is abandoning its cashierless checkout system at its chain of fresh grocery stores due to reliance on human monitors.
The 'Just Walk Out' system used cameras and sensors to track customers and charge them automatically.
About 70% of 'Just Walk Out' sales required human review, indicating the system was not fully automated.
Google has agreed to delete a large store of web data collected while users browsed in Chrome's incognito mode.
Google will update its privacy policy and incognito mode landing page to better inform users about data collection.
Google was sued in a class action lawsuit for data collection practices in incognito mode.
Qualcomm released new benchmarks showing their upcoming ARM-powered Snapdragon X Elite laptop processors.
The X Elite performed around 50% faster and consumed less power compared to Intel's Core Ultra chips.
TSMC announced that operations recovered quickly after Taiwan's strongest earthquake in 25 years.
Australia is turning to virtual fences to address issues with large animal detection systems in vehicles.
A piece of metal from the ISS hit a home in Naples, Florida, possibly making Japan liable for damages.
Transcripts
that's right you know what time it is a
fact I'm going to rely on as I do not
have a watch but I trust you a serious
security back door and a widely used
compression utility for Linux has come
to light after being discovered and
flagged by developer Andres Frey who
works for Microsoft by day and maintains
postgress SQL by night just like Batman
Ry only noticed because he was making
the best of his Easter Long Weekend by
doing some micro benchmarking when he
noticed that encrypted logins to part of
the exed compression Library were using
a ton of CPU which led him to discover
the back door in xed utils God you're
saying Zed did we say Zed in Canada I'll
I'll stop now I'll say it normal had it
not come to light when it did it could
have been potentially disastrous XZ
there you go utils is available for
almost every distribution of Linux but
luckily the malicious code was spotted
before it could be added into the
production release of a major drro it
was however founded beta releases for
Fedora Rawhide and and Debian as well as
a stable release of Arch Linux and the
arch users will inform you of that the
back door apparently works by injecting
coat during SSH authentication thereby
allowing unauthorized remote access
bizarrely this malicious code seems to
have been introduced by one of XZ utils
two primary developers giaan AKA GIA
t75 one of the earlier Terminators who
had been contributing to the XZ project
regularly since 2021 while it's possible
that their system was compromised G t75
is account engaged in suspicious
activity over the course of several
weeks including repeatedly contacting
others about their new fixes several
notable contributors to the project have
therefore theorized the G t75 is
involvement in XZ has been part of a
long con intended to get more and more
invasive permissions through both
genuine code contributions and a
pressure campaign conducted through sock
puppets against its original developer
Lassie Colin for faster development so
far researchers have yet to find any
evidence that gean exists Beyond his
presence in open- Source circles which
honestly isn't all that different from
other Linux users stop browsing the web
using a text editor and go outside your
family misses you you have to see your
family to tell them you use
Arch Amazon is abandoning its
cashierless checkout system at its chain
of fresh grocery stores in part because
it wasn't really cashierless and instead
relied on a small army of over a
thousand overseas workers monitoring and
reviewing footage from these
transactions the program launched in
2016 under the name just walk out the
empowering slogan of absent fathers
everywhere just walk out involves a
series of cameras and sensors throughout
the store which track customers after
they scan in at the door and
automatically charge them for the items
they take when they leave 27 of Amazon's
44 fresh stores have just walk out
available and while Amazon gave the
impression that the system was fully
automated an estimated 70% of just
walkout sales required a human review as
of 2022 according to information from
the information they love that stuff
they do love information Amazon disputes
this number and claims that these
reviewers primary purpose was to
annotate videos for improved machine
learning if accurate however this would
seem to indicate that the company wasn't
actually replacing human cashiers it was
just Outsourcing them most likely by
having an underpaid office worker in
India watch you while you shop this
might explain why Shoppers at Fresh
stores sometimes found it would take
hours to receive a receipt for their
purchase Amazon hasn't given up on the
cashier lless experience though and its
stores will instead increasingly rely on
dash carts essentially a combination of
shopping cart and self checkout which
tallies up items as they're added to the
cart although maybe there's actually
just a tiny little man hiding behind the
screen who uses a peephole to look
inside your cart and see what you're
buying who knows as part of a settlement
to a class action lawsuit Google has
agreed to delete a massive store of web
data that it collects Ed while users
browsed using Chrome's purportedly
private incognito mode Google has
likewise agreed to update their privacy
policy as well as the incognito mode
landing page to explicitly notify users
that the company continues to collect
data from third party sites and apps
regardless of what mode their browser is
in Google originally argued to have the
case dismissed under the logic that
users had implicitly consented to have
their data collected even in incognito
mode because it warned them that their
activity might still be visible to
websites they visit which is a bit like
saying that your wife consented to your
affair because you told her there might
be other women at the company Christmas
party you know how these parties Go I
mean I mean you put some scotch in me
and I put myself in
women in a silver lining for Google the
agreement will spare the company from a
potential $5 billion penalty which is
good because they need that money to
invest in their next project preventing
other people from stealing your browser
data I don't steal their brand Google is
testing to Vice bound session
credentials to block malicious actors
from accessing sensitive accounts by
stealing and cloning a person's session
credentials a form of encryption that
ties authentication cookies to the
user's PC something we here at lmg have
intimate intimate experience with now
it's time for quick bits brought to you
by T the mobile company offering more
data and lowering their prices for every
single plan T's Unlimited Plan offers a
host of features like free international
calls to 60 plus countries free hotspot
and tethering and unlimited 2G data
after you've used your 35 GB 4G LTE 5G
balance all for just 25 bucks a month oh
and forget those binding contracts with
t there's no bulk buying no advance or
annual payment no contracts there's only
the flexibility to build your own phone
plan just the way you like it say tell
to your new phone plan at the link below
so that's how that goes and now it's
half past Tech news also known as quick
bit of clock just some fun Studio lingo
we all say it it's what we call it yeah
I totally didn't make that up Qualcomm
has released new benchmarks showing
their upcoming arm powerered Snapdragon
X Elite laptop processors embarrassing
Intel's recently released meteor Lake
core Ultra chips compared to Intel's
core Ultra 9 185h and core Ultra
755h really cool names the elite
performed around 50% faster in geekbench
at around half the power consumption
also beating out amd's ryzen 9 7940 HS
and even Apple's M3 qualcomm's regularly
been bragging about how great the X
Elite is since October and with the
month to go until they finally arrive on
the new Microsoft Surface lineup I think
it's time to chill for a bit you didn't
see apple chasing people around on the
street with PowerPoint presentations
about how the M1 is going to
revolutionize the industry please please
they left it to the boardrooms all of
them last year Google warned that the
Google podcast service would soon Google
perish and for sooth it has now come to
Google pass how do they know users
outside of the US will still be able to
listen to podcasts until June 24th but
after that everyone will have to get
their fix somewhere else like on app
that Google hasn't killed yet YouTube
music hopefully you don't go looking on
that app for Google's Z made by Google
podcast though because YouTube music
doesn't have it Google if if you're
going to kill so many apps it would be
nice to have more of a plan than the
Star Wars sequels no why did don't
mention it oh it hurts tsmc has
announced that workers are already
returning to factories less than 24
hours after Taiwan was hit by its
strongest earthquake in 25 years as a
reporting the Quake killed nine and
injured more than 1,000 people 70% of
tsmc's chipm operations had recovered
within 10 hours of the earthquake and
that is unfortunately important because
Taiwan is responsible for 80 to 90% of
the world's high-end chips but I think I
speak for the world when I say hey tsmc
come here new chips are nice and all but
so is taking a single day off after your
country was devastated by an earthquake
having said that um thanks for
preventing a domino effect that would
inflate the price of basically
everything on Earth even further so back
to work Australia is turning to Virtual
fences after mult mulle car companies
have tried and failed to calibrate their
onboard large animal detection systems
to kangaroos they already had large
animal detection systems Volvo for
example has had a system that detects
pedestrians cyclists and various sunry
Beasts of the forest since 2016 but
kangaroos have proven a bit of a problem
in part because the average pedestrian
can't run at 44 mph or launch themselves
10 ft into the air not with that
attitude according to Volvo Australia's
Tech technical lead David picket
kangaroos tend to move unpredictably and
when it's Airborne you lose the point of
reference for where it actually is
terrifying instead Australia will be
experimenting with virtual fences which
are activated by approaching headlights
and use flashing lights and high-pitched
alarms to scare animals away from
roadsides installation is unfortunately
expensive but on the other hand a
kangaroo hitting your windshield is both
expensive and bad for the kangaroo does
that mean that driving down a highway in
Australia will sound
like a piece of metal discarded from the
International Space Station apparently
ripped through the roof and two floors
of a home in Naples Florida and if you
felt relieved after I specified which
Naples it was you're a bad person the 2B
piece of cylindrical metal that hit the
home of Alejandro Otero is alleged to be
part of a 2.9 ton cargo pallet
containing nine batteries tossed from
the ISS 3 years ago apparently Japan may
be liable for the damages since their
space agency sent the now discarded
structure into space so congratulations
to whoever had Florida man Su Japan
after extraterrestrial attack on their
2024 bingo card but if you've got more
Tech news on your bingo card just come
back on Friday when we post the next
episode if you don't play Bingo very
simple you should instead come back on
Friday when we post the next episode
don't do the other one don't mix them up
5.0 / 5 (0 votes)