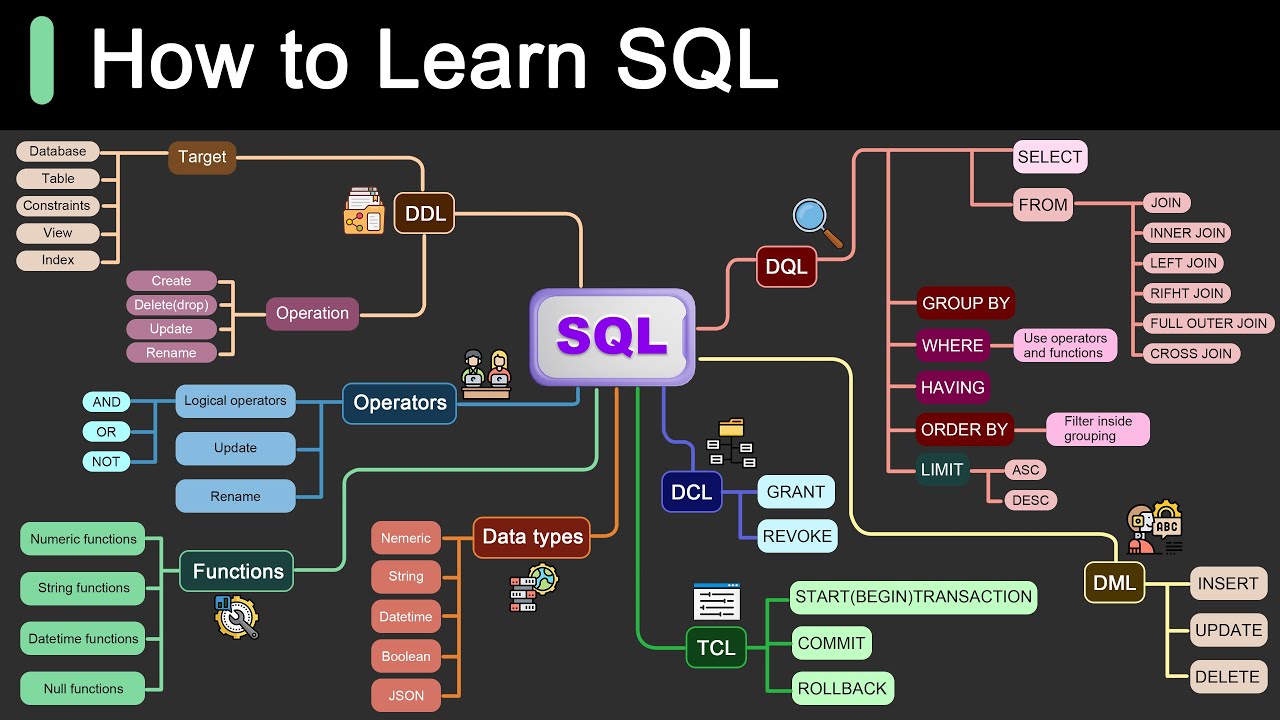
Memory Forensics Using the Volatility Framework
Summary
TLDR本视频展示了如何使用易变性框架对感染了Crydex恶意软件的Windows XP机器的内存转储进行分析。教授K通过创建文件夹、下载恶意软件样本、使用不同插件(如ps list、ps tree、conscan、netscan和sockets)来识别运行中的进程、隐藏的进程、活动套接字和开放的连接。通过分析,发现了一个可疑的进程reader_underscoresl.exe,它与explorer.exe有关联,并且通过POST请求与特定IP地址通信。通过VirusTotal网站的在线检查确认了该可执行文件为恶意软件。进一步的注册表分析揭示了恶意软件通过修改启动注册表项来实现每次启动时自动运行。
Takeaways
- 🔍 使用Volatility框架进行内存分析,可以帮助识别和分析恶意软件。
- 💻 实验室演示使用了Windows XP机器的内存转储,感染了名为Crydex的恶意软件。
- 📂 创建一个文件夹用于存放和分析内存转储文件,例如在桌面创建名为'memdump'的文件夹。
- 🔗 通过开源位置下载Crydex恶意软件样本,以便进行分析。
- 🖥️ 使用CSI或Linying等工具来分析内存样本。
- 🛠️ 利用Volatility框架的'pslist'和'pstree'插件来查看运行中的进程。
- 🔎 识别可疑进程,如'reader_underscoresl.exe',它可能与恶意软件有关。
- 🌐 使用'conscan', 'netscan'和'sockets'插件来检查运行中的套接字和开放的连接。
- 📊 通过命令行插件查看在内存转储期间执行的命令,以追踪可疑活动。
- 🔒 使用'strings'命令来检查内存中特定进程的数据,寻找潜在的恶意行为证据。
- 📋 通过在线服务如VirusTotal来验证可疑文件是否为恶意软件。
- 🔄 分析注册表,确定恶意软件如何被启动,以及如何通过修改启动项来持续存在。
Q & A
本次视频中使用的记忆分析工具是什么?
-本次视频中使用的记忆分析工具是Volatility框架。
教授K在视频中分析的恶意软件样本名称是什么?
-教授K在视频中分析的恶意软件样本名称是CryDex。
在进行记忆分析之前,教授K首先创建了一个名为什么的文件夹?
-在进行记忆分析之前,教授K首先创建了一个名为'memdump'的文件夹。
教授K是如何获取到CryDex恶意软件样本的?
-教授K通过访问开源位置的网站,从该网站下载了CryDex恶意软件样本。
在Volatility框架中,教授K使用了哪个插件来获取关于内存转储的详细信息?
-在Volatility框架中,教授K使用了'imageinfo'插件来获取关于内存转储的详细信息。
在分析过程中,教授K发现了哪个可疑进程?
-在分析过程中,教授K发现了一个名为'reader_underscoresl.exe'的可疑进程。
教授K使用了哪些Volatility插件来检查运行中的套接字和开放的连接?
-教授K使用了'conscan'、'netscan'和'sockets'三个Volatility插件来检查运行中的套接字和开放的连接。
在检查注册表时,教授K发现了哪个启动项可能是恶意的?
-在检查注册表时,教授K发现'kb0020787.exe'可能是恶意的启动项。
教授K如何确认reader_underscoresl.exe是恶意软件?
-教授K通过使用在线网站VirusTotal来检查reader_underscoresl.exe,并确认它是恶意软件。
教授K在视频中提到,如果不及时清除恶意软件的启动项,会有什么后果?
-如果不及时清除恶意软件的启动项,每次系统启动时,恶意软件都会被重新生成或替换,导致病毒扫描器无法彻底清除。
教授K在视频中建议如何彻底删除CryDex恶意软件?
-教授K建议除了删除恶意执行文件外,还需要清除启动注册表项,以防止恶意软件在每次启动时重新生成。
Outlines
🔍 实验室准备与Volatility框架介绍
本段介绍了实验室的准备工作,包括创建工作文件夹、使用CSI工具(或类似的工具)进行内存分析。教授K将使用Volatility框架来分析一个感染了CryDex恶意软件的Windows XP机器的内存转储。首先,教授K指导如何在桌面创建一个名为'memdump'的文件夹,并展示了如何下载恶意软件样本和提取到指定文件夹。接着,通过终端启动Volatility框架,并使用'volatility -f'命令结合'imageinfo'插件来获取内存转储的详细信息,确定其来源。
📋 分析进程列表与识别可疑进程
在这一段中,教授K继续操作Volatility框架,使用'pslist'和'pstree'插件来查看Windows XP机器上运行的进程。他指出,虽然有些进程是正常的Windows操作系统功能,但有些如'explorer.exe'和未知的'reader_sl.exe'等进程需要特别注意。通过'psxview'插件,教授K检查是否有进程试图隐藏。虽然没有发现隐藏进程,但他通过'conscan'、'netscan'和'sockets'插件检查了运行中的套接字和开放的连接,发现了两个使用PID 1484的连接。
🔎 深入分析可疑进程与恶意软件确认
在这一部分,教授K通过命令行插件'cmdline'和内存转储插件'dump'来分析与'sreader_sl.exe'进程相关联的命令。他发现'explorer.exe'与'reader_sl.exe'有关联,并通过'strings'命令进一步分析了该进程的内存内容,揭示了该进程试图通过POST请求将信息发送到IP地址41.168.5.140。为了确认'sreader_sl.exe'是否为恶意软件,教授K建议使用在线服务如VirusTotal进行检测。结果显示,32个病毒扫描器中的72个将其识别为恶意软件。
🛠️ 恶意软件启动机制分析与解决方案
最后一段中,教授K探讨了如何通过分析注册表来确定恶意软件的启动机制。他使用'hivelist'插件列出了目标机器上的注册表蜂巢,并通过'-k'参数查看了启动时运行的键值。他发现了'kb0020787.exe'在启动时被注册表指定运行,这可能是恶意软件重新加载的原因。通过进一步分析,教授K确认了'kb0020787.exe'与PID 1640的进程有关联,揭示了恶意软件如何每次启动时重新加载。他总结了如何从受感染的机器上删除此恶意软件,并结束了这段关于使用Volatility框架进行内存分析的视频演示。
Mindmap
Keywords
💡挥发性框架(Volatility Framework)
💡内存转储(Memory Dump)
💡Crydex恶意软件
💡进程列表(Process List)
💡注册表(Registry)
💡恶意软件分析(Malware Analysis)
💡数字取证(Digital Forensics)
💡网络扫描(Netscan)
💡字符串命令(Strings Command)
💡病毒总计(VirusTotal)
💡启动项(Startup Entries)
Highlights
使用易挥发性框架(Volatility Framework)进行内存分析
分析从感染了Crydex恶意软件的Windows XP机器上捕获的内存转储
使用CSI Lining或其他内存分析工具进行实验室演示
创建工作文件夹并下载恶意软件样本
使用Volatility框架提取内存转储文件
确定内存转储的配置文件,这里是Windows XP SP2
使用ps list插件查看运行中的进程列表
识别可疑进程,如reader_underscoresl.exe
使用ps tree插件进一步分析进程树
检查隐藏进程,但没有发现任何试图隐藏的进程
使用conscan、netscan和sockets插件检查运行中的套接字和开放的连接
发现使用PID 1484的两个连接和套接字
使用命令行插件查看CLI上运行的命令
揭示explorer.exe与reader_underscoresl.exe之间的关联
使用strings命令检查可疑可执行文件的内存内容
发现可疑可执行文件与特定IP地址的POST请求通信
通过VirusTotal确认reader_underscoresl.exe是恶意软件
探索注册表以确定恶意软件如何在启动时被加载
发现kb0020787.exe在启动时被加载,与PID 1640相关联
总结了如何使用Volatility Framework进行内存分析的步骤
Transcripts
greetings i'm professor k and in this
short video presentation
we'll be doing a memory analysis using
the
volatility framework and in this lab we
will use the volatility framework to
analyze a memory dump captured
from a windows xp machine infected with
malware known as crydex
for this lab demonstration i will be
using csi lining so cali linings could
also be used
the steps in the lab are the same
regardless
so the first thing we want to do is just
go ahead and make a folder that we can
work in
to do this i'm just going to right click
on my desktop here i'm going to select
create folder and i'm going to call this
memdump
just like that go ahead and create leave
that there
and let's go on up to our linings quick
launch
and from here we're going to launch our
web browser in the address bar
i'm going to input the address for the
open source location for different
memory samples go ahead and hit enter
now once you're on the site just scroll
on down until you come to
the option to download the malware
cridex
sample let's go ahead and double click
it
and it downloads very quickly the next
thing you want to do is just go on over
here to your preferences
open that up and from your preferences
select
to view your downloads and from your
downloads
you're going to see that you have
downloaded the memory dump
but we need to go ahead and keep it so
go ahead and select that option to keep
then it's going to ask you one more time
you're going to say keep anyway
and now you can show in folder now once
you have
the memory dump in the download folder
available to you just right click on it
and from the context menu you're going
to select the option to
extract to from here you're going to
select the location for your desktop
and then from there you're going to
select the location for that new
directory we've created
called memdump just go ahead and double
click that or open it up
and then scroll on down over here to the
bottom right and click on the button
that says extract
once you've done that you can close out
everything return to your desktop
now what you can do is right click on
that directory we created
earlier called memdumps just right click
on it and you're going to select open
terminal here let's go ahead and make
that full screen
to launch our volatility framework at
the prompt i'm just going to type in
the letters v o l
and then i'm going to hit my tab key one
time
and that's going to give me the options
that i can choose from
that are available to me to complete the
spelling of the tool that i need to
access
in this case is volatility so now i'm
just going to add an
a and now i'm going to press tab one
more time
and the command is completed once i have
the name for
volatility at the prompt i'm just going
to
finish off the command by pasting the
following
dash f which stands for use the
following file
and the file i want to use is critex.vm
and space image info so we want to get
as much information about this memory
dump that we're going to analyze as we
possibly can
in this case i want to establish where
the memory dump came from
and any other information i can have
that will help fill out
the profile i'm going to go ahead and
hit enter
and in just a moment it comes back with
the
determination of the profile from which
our memory dump came from now in this
case
we're looking at a windows xp machine
with service pack
2. so for most of the remainder of the
lab
i will be just bringing up the previous
command
with my up arrow and i will be putting
in another plug-in
image info for example is a plug-in that
is used with
the volatility framework and that's what
we're going to be replacing as we go
through this lab
is the plugin so i've got my command
all established here and i've typed in a
volatility
again dash f for use the following file
but i've also added the profile and so i
want the profile
that is going to be used against this
memory dump
so that it can find the information that
we're looking for
so i've typed in dash dash profile
equals
that's just the name of the profile that
volatility believes belongs to our
memory dump
give it a space and the first thing we
want to look at is the process list
so i've typed in ps list go ahead and
hit enter
and so you can see at the time that this
memory dump was captured
all the processes that were running on
this windows xp machine
and as you scroll through this list of
processes you have to be aware
of any that catch your attention some of
these are just going to be normal
processes that are going to run
and that's just the way windows
operating system
functions but when we see processes that
are running such as explorer
and an unknown processor called
readerunderscoresl.exe
these are the processes that you need to
give your attention to i've cleared my
screen
and another plug-in that we can use to
view the processes running on our
windows xp
machine is ps tree
go ahead and run that real quick now
you'll notice
there's something peculiar here and you
gotta take a look at it
is it's that this root process
right here for explorer has another
process
running just beneath it called the
reader underscore sl.exe
let's go ahead and clear our screen one
way we can determine if something may be
malicious on our computer when we're
doing this memory scan
is to see if there's any processes that
are
currently trying to hide so to do this
i've typed in
p s x view and this will show us any
processes
that are trying to hide and not be
discovered
now we have to look at the first two
columns the ps list
and the ps scan if any of those register
as false then that process is attempting
to hide
in our case we don't see anything that
tells us
that any process is currently trying to
hide from our view
i'm going to go ahead and clear my
screen now that we have identified our
running processes
we can next check for any running
sockets and open connections
to do this we will call upon three
different volatility plug-ins
conscan netscan and sockets now the
first plugin we're going to run
is the con scan go ahead and hit enter
with that
give it a moment and it comes up and it
tells us
that during this processing of capturing
this memory dump
there were two connections that were
currently running
using the pid of 1484.
we next want to look at any running
sockets that are currently available
during the capture of this memory dump
so i've just replaced the
plug-in con scan with the plug-in
sockets i'm going to go ahead and hit
enter
and it comes back and it shows us all of
the sockets that are currently running
and what process id is currently
involved
and so what draws our attention here to
the sockets is
the one that is using process id of 1484
running on port 1038 using tcp
we can attempt to run the netscan module
against this memory dump but the problem
we're going to run into
is that this profile is too new
and the memory dump is probably too old
and therefore it probably won't work
and it comes back that this command does
not support the profile
of a windows xp machine running service
pack 2.
let's go ahead and clear our screen and
now we're going to switch on over to
three other plug-ins
that we need to run across this memory
dump and the first one is going to be
command line we want to see what
commands were ran from the cli
on this particular memory dump so let's
take a look at that real quick
so far we know that the explorer.exe
with a process id of
1484 we see that right here in the
command line
is directly associated with the
process id 1640 which is running the
reader underscore sl.exe program
and we see that here so now that we have
identified a link between explorer.exe
and the readerunderscoresl.exe
and how they are associated with each
other and now that we have
the complete path for how these two
programs are
actually being brand we're starting to
look at this readerunderscoreasl.exe
with a little bit more scrutiny
so let's go ahead and clear our screen
using the following command i'm able to
dump out the memory area that runs this
executable
up inside of this memory dump and we can
take a closer look at
exactly what's going on behind this
process
of 1640 running the reader underscore
sl exe executable now what i'm telling
it here to do is to dump out that part
of the process
from the memory dump and put it into the
root directory that's what the period
does
and so this first command we created a
dump of the executable
called 1640 for lack of a better term
and we now have that up inside of our
root folder
we next need to look at the addressable
memory that was being utilized
by the executable so in this example
what we're doing is we're pulling out
all the available information we can
about the process id 1640 that is
running
and is associated with that executable
readerunderscoresl.exe
go ahead and hit enter and so now we're
hoping that we'll be able to look
closer at what was going on inside of
the
memory where this reader underscore
asl.exe
was running now to do this we're going
to use a strings command
that is pretty common inside of linings
so i've typed in the following command
strings
space the name of the file 1640.dmp
and that's the dump file that we just
created
whoops i gotta take out that dollar sign
let me use my up arrow
and let's get rid of that all right
let's get back up here to the front
and we're gonna hit enter we use the
correct command combined with the dash
capital c followed by the number to get
the previous and next lines
thus giving us more context for the
information that was found
here we can clearly see that the
executable readerunderscoresl.exe
is communicating towards the destination
ip address
of 41.168.5.140
using post request potentially
exfiltrating
information from the victim's computer
now this memory dump that we created for
process id 1640
has a lot of information going on inside
of it so
we're going to have to go through it one
page at a time
now to do this we can also use the
strings command
and we're going to tell it what dump or
what file we want to look at and we're
going to give it a space a pipe
and then we're going to use the less
command when we use the less command
we're saying
show me the information one page at a
time
so we're going to go ahead and hit enter
and we can scroll through this
information one page at a time just by
using our space bar
on our keyboard so there's another page
there's another page
and we come down to this long list of
banking urls
so we've got a lot of suspicions going
on here about this reader underscore
asl.exe
but we need to confirm our suspicions by
seeing if this is actually a piece of
malware
now to do this we could either reverse
engineer
the executable which none of us have the
expertise to do
or we can just use an online website
such as virustotal
to examine it for us and give us back
the information we're
seeking so let's just go ahead and
minimize our terminal
and now we're going to go over here to
our lining quick launch and we're going
to launch a web browser
in the address bar of our browser we're
just going to tell it to go to
virustotal.com
and we're going to hit enter and once
we're out here at the virustotal.com
site we're just going to make sure that
we've got files selected
and then we're going to use the upload
option so go ahead and
click on the upload option click on your
desktop
make sure you go into your working
folder which is memdumps
and find that executable that we created
from our memory dump and that was
executable.1640.exe
just go ahead and double click it and in
just a moment it comes back and it tells
you
that 32 out of 72 virus scanners
found this to be malicious so we have
determined that the executable
reader underscore sl.exe is a piece of
malware
but what's launching it that's the trick
so now we're going to delve into the
registry and see if we can find out
how this is being launched at startup
let's go ahead and close out our browser
let's stream back up our terminal now to
get out of here all i have to do is just
press q for quit and i'm back to my
prompt
so most malware will look to see if the
infected files are still present
at every system startup sophisticated
malware will also communicate
with the executable every few minutes to
ensure that it is still present
and it has not been removed if it has
been removed they will
rebuild the executable but this time
often they'll use a different name
if you remove the executable without
removing the payload that rebuilds it
each time it is cleaned from the machine
you just keep going in circles granted
oftentimes
you can find a virus scanner that will
find the executable and will remove it
but if it can't find it at startup
and remove the actual payload that is
regenerating
the executable then each and every time
you launch that machine at startup
it's going to rebuild or replace that
deleted malware that you took care of
with your virus scanner
so to see what registry hives are
present on our target machine that we're
pulling this memory dump from
we can use the hive list plugin go ahead
and hit enter
and now we have our registry hives but
what we need to find
is what is hiding in one of the keys
that is running as an executable at
startup
so that we can see what is actually
launching that reader underscore sl
dot exe all right let's go ahead and
clear our terminal
and this next command that we're going
to run is going to allow us to look at a
specific key
and we get that with the dash k switch
and up inside of here we're going to
look for what is
running at startup so we're looking at
the software
microsoft windows current version run
key that's the one we want to analyze so
i'm going to go ahead and hit enter
so you got to take a look at what's
actually running at startup
if it's a system service well that's
normal
but if it's launching an executable that
may not be normal
so you got to take a closer look at that
now to do this we're going to scroll on
down through the hives here
and see if we can find anything that's
going to give us some information about
who or what may be launching this
executable
and here we see a kb0020787.exe
that is being launched at startup under
the profile of someone named robert
and we see that this is up inside of the
application data
that's where it's located and the
registry is telling it
to launch this at each startup there's
our culprit right there
let's go ahead and clear the screen now
what we have to do
is see if there's any association with
that kb
executable that we just discovered and
our running process
of 1640. if there's a link between the
two
then we know we have found what is
actually
reloading that malware every time we
delete it
we're going to pull this information out
of the memory dump that we created
for the process of 1640. so if anything
is found
in regard to that kb executable inside
of the 1640
well then there's our link and rather
quickly we're shown that the executable
kb00207877.exe
is directly associated with the process
id of 1640.
so we're pretty certain now that the
krydx malware
modified the startup registry to include
the launching of this executable each
time the machine started up
this should tell us how we can delete
this
executable this malware from the user's
machine or any machine on the network
that is currently infected
with crydex
and so that's going to conclude this
short video presentation on how we go
about performing
memory analysis using the volatility
framework
you got questions you got concerns don't
hesitate to reach out and contact your
instructor and i'll see you in my next
video
5.0 / 5 (0 votes)