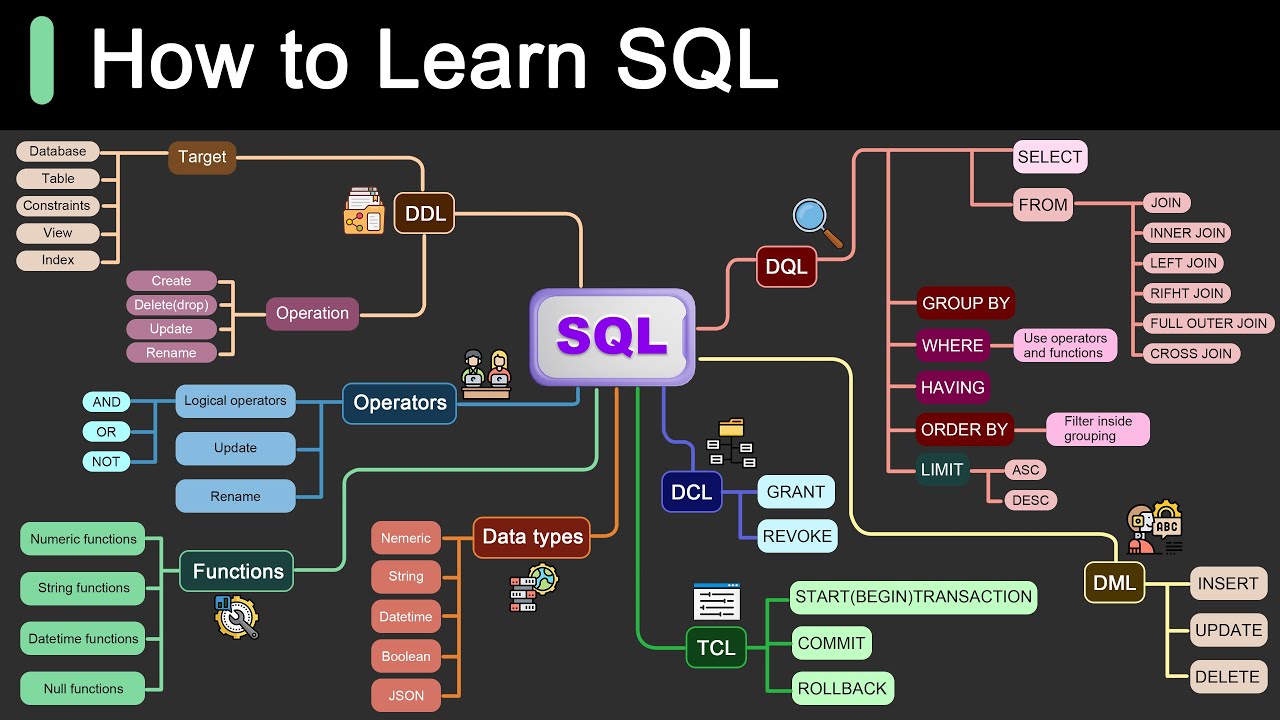
Understanding the Linux Backdoor: Implications for Open Source [When Penguins Cry]
Summary
TLDR在这段视频中,Dave,一位退休的微软操作系统工程师,讨论了一个新发现的SSH后门漏洞,该漏洞被插入到Linux系统中。这个后门允许持有私钥的攻击者无需密码即可登录任何受影响的Linux服务器,并获得根访问权限。幸运的是,这个后门在造成广泛影响之前被一位微软员工发现,他在进行PostgreSQL数据库的基准测试时注意到SSH登录时间异常。Dave还探讨了开源和闭源系统在防止此类后门方面的优劣,指出尽管开源代码可以被任何人审查,但并非所有代码,特别是像XZ utils这样的小众项目,都会得到应有的关注。他强调了严格的商业发布流程,如Windows NT所采用的,如何通过多层次的代码审查和验证测试来捕捉这类问题。此外,Dave还分享了自己在微软实习期间的一次后门事件,强调了代码审查的重要性。
Takeaways
- 🚪 存在一个SSH漏洞,可能允许攻击者登录任何Linux系统。
- 🔑 漏洞涉及一个后门私钥,它被嵌入到SSH中,使得持有相应公钥的人可以无需密码登录。
- 🧩 这个后门是通过XZ utils的代码提交引入的,影响了5.60和5.61版本。
- 🔍 尽管代码本身没有修改,但通过Makefile注入了加密压缩的二进制数据,这在源代码审查中很难被发现。
- 🛡️ 如果这个后门没有被及时发现,对Linux系统来说将是灾难性的。
- 👀 一个在微软工作的PostgreSQL数据库基准测试人员注意到SSH登录时间变长,从而揭露了这个后门。
- 🤔 开源和闭源系统在防止此类后门方面哪个更安全,是一个值得探讨的问题。
- 📈 在商业发布中,代码变更会经过多层次的审查和验证测试,这有助于及早发现问题。
- 👥 在Linux中,如果变更涉及到许多人关心的部分,可能会受到更多的审查。
- 📚 作者在微软的实习经历中,有一个实习生在MS-DOS的复制命令中添加了一个特殊开关,这在源代码变更审查中被发现。
- ✅ 微软在作者任职期间据其所知没有被插入过任何后门,这可能归功于严格的审查流程和一些运气。
Q & A
视频中提到的Linux后门是如何工作的?
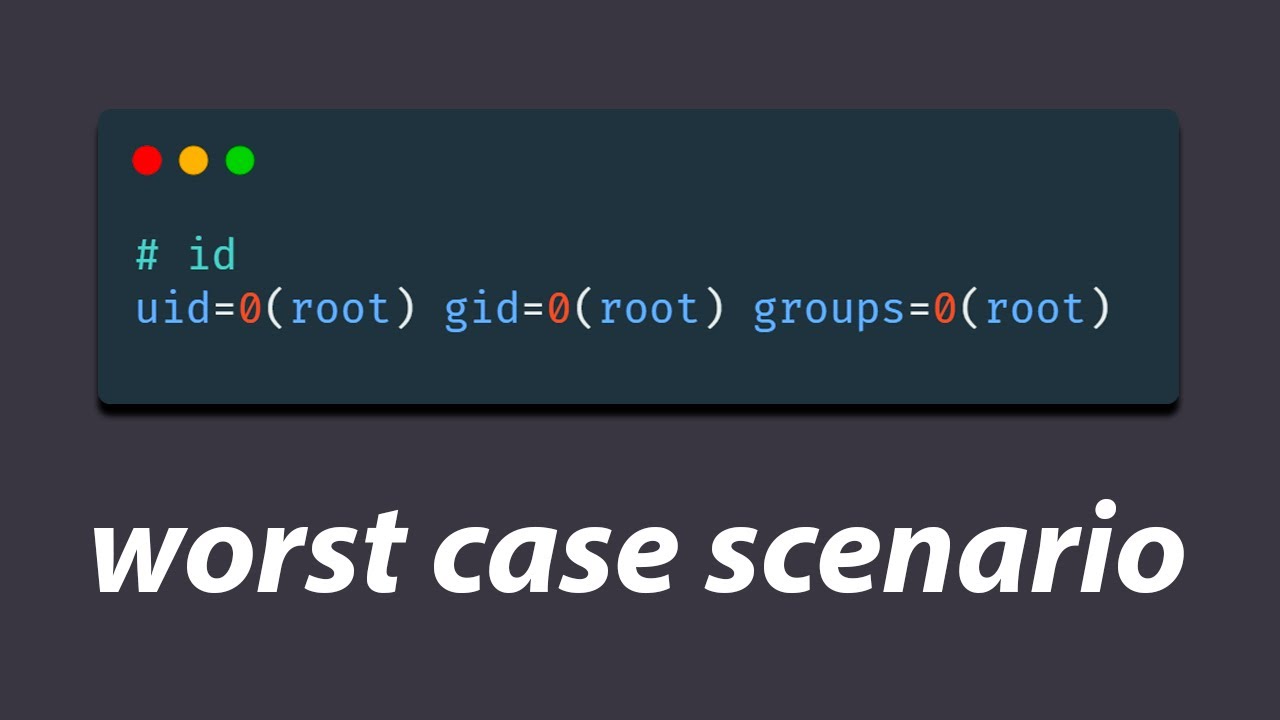
-视频中提到,攻击者在Linux系统中插入了一个后门,该后门通过在SSH中查找一个私钥,并内置一个公钥。任何拥有这个私钥的人都可以无需密码就能通过SSH连接到任何带有该后门的Linux服务器,并获得root访问权限,从而对系统进行无限制的操作。
这个后门的潜在影响是什么?
-如果这个后门没有被及时发现,其潜在影响将是灾难性的。攻击者可以利用这个后门对任何受影响的Linux系统进行完全控制,这对于系统的安全性和用户的隐私权都是极大的威胁。
这个后门是如何被插入到Linux系统中的?
-后门是通过在XZ utils的5.60和5.61版本中插入代码实现的。开发者没有修改源代码,而是注入了加密和压缩的二进制数据,这些数据通过make文件在构建过程中被解密并插入。这意味着源代码审查不会发现任何变化,从而隐蔽了后门的存在。
这个后门是如何被发现的?
-一个在微软工作的基准测试人员在进行PostGIS数据库测试时,注意到SSH登录时间突然变长,这引起了他的注意。他深入研究并发现了这个后门,随后公布了这一信息。
开源系统和闭源系统在防止此类后门方面哪个更有优势?
-视频作者认为,在这种情况下,源代码的开放性并不是最关键的因素。开源系统的make文件和源代码一样公开,但可能没有得到足够的审查。而在闭源系统中,如Windows NT,代码变更需要经过多层次的审核和测试,这可能更有助于早期发现并阻止此类后门的出现。
视频作者在微软的工作经历中有没有遇到过类似的情况?
-视频作者在微软实习期间,有一个实习生同事在MS-DOS项目中尝试插入一个特殊命令行开关,用于打印不当信息。这个行为在源代码审查中被发现并阻止了。作者在微软的30年经历中,据他所知,Windows没有被插入过类似的后门。
如何保护自己的Linux系统不受此类后门的影响?
-用户应确保不使用受影响的XZ utils版本,并及时关注相关安全公告和更新。同时,可以通过审查系统的SSH配置和日志来检测是否有异常登录行为。
视频作者对于开源社区在审查代码变更方面的看法是什么?
-作者认为,开源社区中的代码变更审查可能不如商业闭源系统那样严格。特别是在不太受关注的项目部分,如XZ utils,可能不会得到应有的审查。
在微软工作期间,代码变更的审查流程是怎样的?
-在微软,代码变更需要经过多层次的审查和测试。首先,有一个专门的构建实验室会独立构建变更,然后通过基本构建和基本验证测试(BVTs)来确保功能正常和性能没有下降。这种严格的流程有助于早期发现并阻止潜在的问题。
视频作者对于防止此类后门出现的建议是什么?
-作者建议,无论是开源还是闭源系统,都需要有严格的代码审查流程和测试机制。同时,开发者和维护者需要对代码变更进行仔细的审查,以确保系统的安全性。
视频作者提到的“幸运”在防止后门方面扮演了什么角色?
-作者认为,尽管有严格的流程和审查,但很多时候防止后门的出现还是依赖于一定的运气。这意味着不能保证所有的安全问题都能被发现,但良好的流程和审查可以最大限度地减少这种风险。
Outlines
😀 Linux SSH后门漏洞及其影响
本段落介绍了Linux系统中新发现的SSH后门漏洞。该漏洞允许攻击者使用私钥登录任何受影响的Linux系统,无需密码即可获得root权限。该后门是通过XZ utils的5.60和5.61版本中的代码变更引入的,但并未广泛传播。发现该漏洞的是一位在微软工作的基准测试人员,他注意到SSH登录时间异常。尽管Linux是开源系统,但该漏洞的隐蔽性表明,即使是开源代码的审查也可能遗漏某些问题。
🤔 开源与闭源系统的安全性比较
该段落讨论了开源系统与闭源系统在防止后门漏洞方面的安全性。尽管开源代码可以被任何人审查,但实际上很少有人会去审查构建过程中的make文件。相比之下,像Windows NT这样的商业软件会经过更多的审查和测试流程,这有助于及早发现问题。作者通过自己在微软的经历,说明了严格的代码审查和测试流程的重要性,以及它们如何帮助维护软件的安全性。
📚 个人经历与后门故事
在最后一段中,演讲者分享了自己在微软实习期间的个人经历,其中包括一个实习生在MS-DOS的复制命令中添加了一个特殊的命令行开关,用以恶作剧。这个行为最终在代码审查中被发现,而演讲者本人并不知情。这个小插曲说明了即使是在严格的审查流程下,也可能有人试图引入不当的代码。幸运的是,该行为被及时发现,没有造成更大的影响。
Mindmap
Keywords
💡Linux
💡SSH
💡后门
💡XZ utils
💡私钥和公钥
💡开源与闭源
💡代码审查
💡构建过程
💡性能基准测试
💡make文件
💡安全漏洞
Highlights
存在一个SSH漏洞,可能允许攻击者登录任何Linux系统
该漏洞是插入到Linux SSH中的一个后门,如果未被及时发现,后果将不堪设想
后门通过在XZ utils中嵌入公钥,允许持有私钥的人无需密码即可登录
攻击者可以获取任何受影响Linux系统的root访问权限
后门代码通过Makefile注入,不修改源代码,因此难以通过源代码审查发现
XZ utils的5.60和5.61版本中存在该后门,但未广泛传播到主流Linux发行版
非主流版本用户如果不使用最新版本,可能不会受到该后门的影响
一个在微软工作的Postgres数据库基准测试员发现了SSH登录延迟的问题,进而揭露了这个后门
开源系统和闭源系统在防止后门方面都有各自的优势和挑战
在微软,代码变更会经过多层次的审查和测试,以确保性能和安全性
在Linux中,代码审查可能不如商业软件严格,尤其是关注度较低的部分
作者在微软实习期间,一个实习生在MS-DOS中添加了一个特殊的命令行开关,作为恶作剧
该恶作剧被发现并导致该实习生未能继续在微软工作
作者认为,尽管有可能存在未被发现的后门,但微软Windows系统并未被证实有后门
微软通过严格的代码审查和变更流程,确保了产品的安全性
作者强调了审查流程和检查平衡的重要性,以及它们在防止不当行为中的作用
尽管存在严格的流程,但不能保证发现所有的安全问题,但可以大大减少风险
Transcripts
so I don't want to scare you but did you
know that somebody checked a back door
into Linux that allows the attacker to
log into any Linux system I'll tell you
about that and I'll also tell you about
the time somebody tried to check a back
door into Ms Doss and did it from my
office that's a cool
[Music]
story hey I'm Dave welcome to my shop
I'm Dave plumber retired operating
systems engineer from Microsoft going
back to the MSDS and Windows 95 days and
today we're going to talk about the new
SSH vulnerability back door that's been
inserted into Linux what it means how it
works and what the implications are and
whether open source is any better off
than closed source and these types of
scenarios first off obviously I'm not a
Linux developer I mean I write code for
Linux but I've never contributed at
least not since about 1993 when I
checked in a bugfix to was it Minix I
think it was early Linux um or email the
I should say but suffice to say I'm not
a Linux contributor or developer so
while I may not be a Linux expert that's
probably good for you right now cuz I
have to explain things in terms that I
understand which means you will likely
understand them as well so before we
look at what happened first what are the
implications what does this back door do
somebody checked in some code and it
looks for a private key and it has a
public key built into SSH and what are
the implications well to put it simply
catastrophic had this not been detected
as early as it was it would have been
truly catastrophic for Linux because
let's say that this this is a nation
state what they've done is they've built
a backdoor private key into SSH that
anybody with the public key or actually
vice versa they put the public key in
the product and then they hold the
private key anybody who holds that
private key and only that person nobody
else can use this exploit I should be
clear about that only if you hold the
private key which the original person
who inserted the back door does then you
can connect to any Linux server with
this back door inserted in fact you
don't need a password you just need to
connect by SSH and the SSH server will
say hey you've got the right private key
in your metadata or whatever extra data
is sent along with login request it
matches that logs you right in basically
not only a completely open door it's
even better than that because it gives
you root access
I that side of it's a little more
technical but suffice to say the result
is that you get unfettered access to any
Linux system in the world that you want
that's running this exploit and you get
rud access so how' they do it well what
they did is they checked code into XZ
utils and when I'm saying they I'm
talking about one of the main developers
of the XZ utils the good news is this is
in 5.60 and 5.61 versions of the XD
utils and that's pretty much bleeding
edge it did make it into a few very
early drops of dros but not it's not
going to be like in 20.04 won't be
picked up immediately or anything into
there so if you're not running on the
bleeding edge long story short you're
probably
safe but surely you can't put a price on
your login safety I wouldn't have
thought so either but here we are so
they checked code into xzu tills that
long story short bakes the public key
into SSH and then accepts connections
from anybody with the private key but
wouldn't that be obvious it seems like
this should be obvious and easy to
detect just by reviewing the source code
change logs but in fact it's not because
they were very clever about how they did
it they didn't modify the source code at
all instead they injected encrypted and
compressed binary data that is decrypted
and then inserted into the build process
via the make file for the XZ tills if I
understand it correctly but this means
there's no changes to the code so
anybody reviewing the source code
changes doesn't see any change and who
reads make file changes I mean they're
pretty obtuse and opaque to begin with
and if you have any idea what a make
file is doing it's either a simple make
file or you're having a really good day
because a lot of make files are pretty
complex and hard to follow once you get
to a certain complexity of a project so
at this point we've got a back door in
the Linux source code and all we have to
do or all they have to do is wait for it
to be propagated through out all the
builds and dros and trickle down
everybody and if it doesn't get caught
before that boom hey by the way one
thing I've noticed lately on YouTube is
that people are like bang ending their
videos immediately and I guess this must
appease the algorithm in some way so I'm
going to do that today which means if
I'm going to tell you the stuff that I
tell you at the end of every episode I
have to tell you now like halfway
through so here it is I'm mostly in this
for the subs and likes so if you're
finding today's episode to be any
combination of informative or
entertaining please leave me one of each
before you go today and if you or
anybody you know is on the Spectrum then
please check out the free sample of my
book on Amazon where I tell you
everything I know about autism that I
wish I'd know in way back then so who
caught it
Microsoft well not really Microsoft guy
that works for Microsoft also happens to
do benchmarking and so on on the postgis
database and he was running his tests
and he noticed that the SSH logins were
taking a lot longer than they used to
and this happened all of a sudden so he
dug into it and he's the hero that found
the information and the back door and
published it and let us all know about
it so had it not been for that this
would have likely been uncaught now of
course this promps the bigger question
of which is more protective against this
type of back door an open source system
or a closed Source system and I'd say in
this case the source code actually isn't
all that relevant of course it's open
but so is the make file was anybody
really scrutinizing the make file and if
they had would they have caught it if
they looked at it carefully well nobody
even at Microsoft is probably hand
reviewing and scrutinizing the make
build code changes unless they cause a
problem if they slow things down they're
going to take a look at it but if you
make changes to the make file and the
binary pops out then everything is cool
it's probably not going to get that much
scrutiny unlike a change to the actual
source code that's going to go through
several layers of review and approval
and again I've been gone for Microsoft
20 years so I'm talking about how we did
it back 20 years ago which was probably
pretty sloppy and lazy and horrible
compared to what they're doing now but
here's the beauty of a regimental
commercial release with something like
Windows NT you don't just check in code
and then wait for it to show up in the
build it goes through a lot of processes
in between first there's a build lab
that picks up just your change build
your change independently builds a build
with your change kicks that out and it
goes through basic build and when all
the changes are collected for the day
that build will go through bvts or basic
verification tests and that's going to
check to make sure that all the normal
stuff works the smoke tests pass the
build boots does everything correctly
and that the performance is not
seriously degraded from previous builds
and that's how it would have been caught
early at Microsoft because the
significant impact to the login chain
would have caused the regression in when
log on if it were you know the
equivalent component in Windows and that
would have been detected immediately now
that's not to say that every such change
would be so it's not a golden guarantee
or anything but the fact that any change
to the product goes through both human
manual review of the textual changes to
the source code and then through a bunch
of verification tests and benchmarks and
several other verification tests that
make sure the functionality and the
performance hasn't regressed that
catches a lot of things it still won't
catch everything be clear on that so
there is no Panacea now the other thing
is when you're checking into code say
I'm checking into the heat manager well
the guy who write wrote The Heat manager
and the person who maintains the heat
manager is going to very carefully check
my changes when you get something like
exz utils I think there was only two
people working on it so did the other
person really vet these changes very
carefully or did lonus you know get out
of his computer and check every line I
doubt that so who is actually vetting
these changes as they go into the build
and the answer is I don't know because
I'm not involved in that process so I
can't really speak to what goes on
behind the scenes in Linux I can only
tell you what used to happen in Windows
how that you extrapolate that forward
and assume they're more careful now and
the protective aspects of that now the
difference is if it's in a part of Linux
that a lot of people care about a lot of
people are going to look at it but if
it's in a part of Linux that a lot of
people don't care about like xzu tills
then it's probably not going to get the
scrutiny that it deserves especially
when you see the implications of how
this change manifests so now a bit of my
own back door stories
when I was an intern in 1993 I was in MS
DOS working on MS DOS 6.2 where I worked
on Smart drive and highe and some of the
compression engine relocation disc copy
setup whole bunch of stuff and there was
a guy in my office that was also an
intern so we shared an office because we
were just interns and he decided that he
was working I believe on the copy
command and he took the opportunity to
check not a back door per se but a
special command line switch so instead
of you know how with x copy SLS we'll do
folder
well with copy he added it so that slart
which is like asky 254 I forget the
actual OEM code page at this moment but
whatever it was he used a special
graphic character and he made that a
command line switch and it would just
print I love sex over and over and over
and over and over and it would print
that out I didn't know anything about
this and then after I'm done my
internship I get a call from my manager
at the time who calls me at home and
says yeah so what did you know about
this and the answer was I knew nothing
and uh naturally they did not invite get
the guy back it was caught in the manual
source code Change review that I spoke
of earlier or however they caught it and
it did not look good for him I don't
know what the repercussions were I don't
know what they did I wasn't involved all
I know is that they took me at my word
that I wasn't involved and thankfully
for that because I want up working on
Microsoft for a long time and I don't
know if I would have hired me after that
little incident in my office did I
really not know about it I didn't so now
in all my time at Microsoft and in the
two decades since over this course of 30
years of Windows and Ms Doss to my
knowledge there has never been a back
door inserted into Windows now it's
possible that one has and it's just
never been found but I would assume that
by now there would be some exploit that
would take advantage of it is that
diligence process Superior coding or
pure luck well I'm going to guess a lot
of it's luck but a lot of it is process
doesn't mean the developers are any
smarter it does mean that people have
day jobs where they are assigned to look
at code changes in other people's
products whether they want to or not
then they are responsible for anything
that happens as a result of those
changes and that makes people pretty
honest and as for the people that aren't
honest there are processes and checks
and balances to make sure they don't do
a lot of harm thanks for joining me see
you
5.0 / 5 (0 votes)